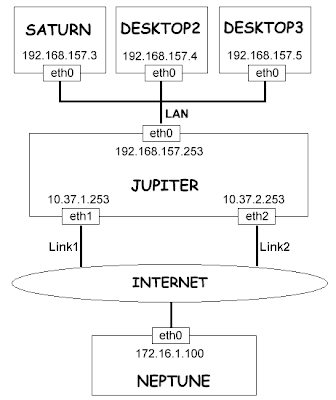
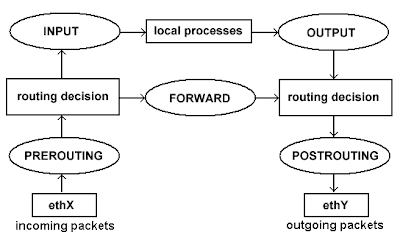
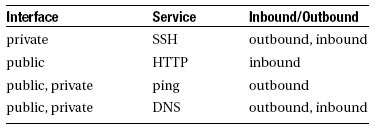
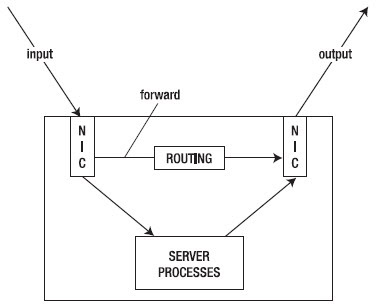
Implementasi QoS (Quality of Services) di Mikrotik banyak bergantung pada sistem HTB (Hierarchical Token Bucket). HTB memungkinkan kita membuat queue menjadi lebih terstruktur, dengan melakukan pengelompokan-pengelompokan bertingkat. Yang banyak tidak disadari adalah, jika kita tidak mengimplementasikan HTB pada Queue (baik Simple Queue maupun Queue Tree), ternyata ada beberapa parameter yang tidak bekerja seperti yang kita inginkan.Beberapa parameter yang tidak bekerja adalah priority, dan dual limitation (CIR / MIR).
Pada pembahasan artikel ini, kita akan mengambil contoh sebuah sistem QoS sederhana, di mana kita ingin mengalokasikan bandwidth sebesar 400kbps untuk 3 client, di mana masing-masing client bisa mendapatkan maksimal 200kbps. Di antara ketiga client tersebut, memiliki prioritas yang berbeda, yaitu: 1,2, dan 3.
Untuk mempermudah pemantauan dan pembuktian, kita akan menggunakan queue tree.
Cara paling mudah untuk melakukan queue dengan queue tree, adalah dengan menentukan parameter :
- parent (yang harus diisi dengan outgoing-interface),
- packet-mark (harus dibuat terlebih dahulu di ip-firewall-mangle),
- max-limit (yang merupakan batas kecepatan maksimum), atau dikenal juga dengan MIR (Maximum Information Rate)
Untuk percobaan awal, semua priority diisi angka yang sama: 8, dan parameter limit-at tidak kita isi. Gambar berikut ini adalah ilustrasi apa yang akan terjadi dengan konfigurasi di atas.
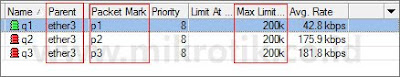
Karena alokasi bandwidth yang tersedia hanya 400kbps, sedangkan total akumulasi ketiga client melebihinya (600 kbps), maka ketiga client akan saling berebut, dan tidak bisa diprediksikan siapa yang akan menang (menggunakan bandwidth secara penuh) dan siapa yang akan kalah (tidak mendapatkan bandwidth yang sesuai).
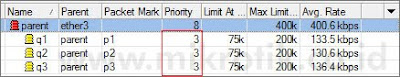
Misalkan q1 adalah client dengan prioritas tertinggi, dan q3 adalah client dengan prioritas terbawah. Kita akan mencoba memasukkan nilai prioritas untuk masing-masing client sesuai dengan prioritasnya.
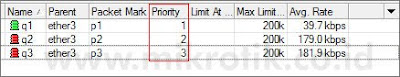
Tampak pada gambar di atas, meskipun sekarang q1 sudah memiliki prioritas tertinggi, namun ketiga client masih berebutan bandwidth dan tidak terkontrol.
Gambar berikut akan mencoba mengimplementasikan nilai limit-at. Seharusnya, limit-at adalah CIR (Committed Information Rate), merupakan parameter di mana suatu client akan mendapatkan bandwidthnya, apapun kondisi lainnya, selama bandwidthnya memang tersedia.
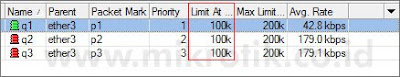
Ternyata q1 masih tidak mendapatkan bandwidth sesuai dengan limit-at (CIR) nya. Padahal, karena bandwidth yang tersedia adalah 400kbps, seharusnya mencukupi untuk mensuplai masing-masing client sesuai dengan limit-at nya.
Berikutnya, kita akan menggunakan parent queue, dan menempatkan ketiga queue client tadi sebagai child queue dari parent queue yang akan kita buat. Pada parent queue, kita cukup memasukkan outgoing-interface pada parameter parent, dan untuk ketiga child, kita mengubah parameter parent menjadi nama parent queue. Pertama-tama, kita belum akan memasukkan nilai max-limit pada parent-queue, dan menghapus semua parameter limit-at pada semua client.
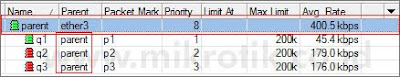
Tampak pada contoh di atas, karena kita tidak memasukkan nilai max-limit pada parent, maka priority pada child pun belum bisa terjaga.
Setelah kita memasang parameter max-limit pada parent queue, barulah prioritas pada client akan berjalan.
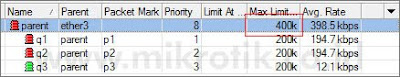
Tampak pada contoh di atas, q1 dan q2 mendapatkan bandwidth hampir sebesar max-limitnya, sedangkan q3 hampir tidak kebagian bandwidth. Prioritas telah berjalan dengan baik. Namun, pada kondisi sebenarnya, tentu kita tidak ingin ada client yang sama sekali tidak mendapatkan bandwidth.
Untuk itu, kita perlu memasang nilai limit-at pada masing-masing client. Nilai limit-at ini adalah kecepatan minimal yang akan di dapatkan oleh client, dan tidak akan terganggu oleh client lainnya, seberapa besarpun client lainnya 'menyedot' bandwidth, ataupun berapapun prioritasnya. Kita memasang nilai 75kbps sebagai limit-at di semua client.
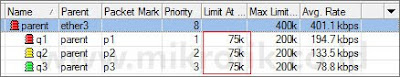
Tampak bahwa q3, yang memiliki prioritas paling bawah, mendapatkan bandwidth sebesar limit-at nya. q1 yang memiliki prioritas tertinggi, bisa mendapatkan bandwidth sebesar max-limitnya, sedangkan q2 yang prioritasnya di antara q1 dan q3, bisa mendapatkan bandwidth di atas limit-at, tapi tidak mencapai max-limit. Pada contoh di atas, semua client akan terjamin mendapatkan bandwidth sebesar limit-at, dan jika ada sisa, akan dibagikan hingga jumlah totalnya mencapai max-limit parent, sesuai dengan prioritas masing-masing client.
Jumlah akumulatif dari limit-at tidaklah boleh melebihi max-limit parent. Jika hal itu terjadi, seperti contoh di bawah ini, jumlah limit-at ketiga client adalah 600kbps, sedangkan nilai max-limit parent hanyalah 400kbps, maka max-limit parent akan bocor. Contoh di bawah ini mengasumsikan bahwa kapasitas keseluruhan memang bisa mencapai nilai total limit-at. Namun, apabila bandwidth yang tersedia tidak mencapai total limit-at, maka client akan kembali berebutan dan sistem prioritas menjadi tidak bekerja.
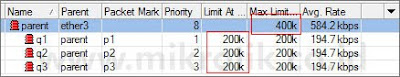
Sedangkan, mengenai max-limit, max-limit sebuah client tidak boleh melebihi max-limit parent. Jika hal ini terjadi, maka client tidak akan pernah mencapai max-limit, dan hanya akan mendapatkan kecepatan maksimum sebesar max-limit parent (lebih kecil dari max-limit client).
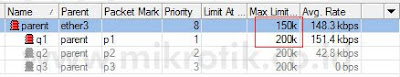
Jika semua client memiliki prioritas yang sama, maka client akan berbagi bandwidth sisa. Tampak pada contoh di bawah ini, semua client mendapatkan bandwidth yang sama, sekitar 130kbps (total 400kbps dibagi 3).
Yang perlu diingat mengenai HTB:
- HTB hanya bisa berjalan, apabila rule queue client berada di bawah setidaknya 1 level parent, setiap queue client memiliki parameter limit-at dan max-limit, dan parent queue harus memiliki besaran max-limit.
- Jumlah seluruh limit-at client tidak boleh melebihi max-limit parent.
- Max-limit setiap client harus lebih kecil atau sama dengan max-limit parent.
- Untuk parent dengan level tertinggi, hanya membutuhkan max-limit (tidak membutuhkan parameter limit-at).
- Untuk semua parent, maupun sub parent, parameter priority tidak diperhitungkan. Priority hanya diperhitungkan pada child queue.
- Perhitungan priority baru akan dilakukan setelah semua limit-at (baik pada child queue maupun sub parent) telah terpenuhi.
Panduan praktis cara perhitungan limit-at dan max-limit
Di asumsikan bandwidth yang tersedia sebesar 1000kbps. Dan jumlah seluruh client adalah 70. Yang perlu diketahui adalah :
- Berapa jumlah maksimal client yang menggunakan internet pada saat yang bersamaan. Jumlah ini belum tentu sama dengan jumlah komputer yang ada, apabila semua client tidak pernah terkoneksi secara bersamaan. Sebagai contoh, untuk kasus ini kita asumsikan adalah 50.
- Berapa jumlah minimal client yang menggunakan internet pada saat yang bersamaan. Sebagai contoh, untuk kasus ini kita asumsikan adalah 10
Maka, untuk setiap client (1 client dibuatkan 1 rule queue), limit-at nya adalah 1000 / 50 = 20kbps, dan max-limit nya adalah 1000 / 10 = 100 kbps.Jangan lupa untuk menambahkan parent dengan max-limit sebesar 1000kbps (tidak perlu limit-at), dan memasukkan semua queue client di bawah parent queue. Jika untuk terminal tertentu membutuhkan priority lebih besar, maka kita bisa menggunakan priority yang berbeda-beda, tergantung dengan urutan prioritasnya.
Sumber : mikrotik.co.id